New theories and technologies for intelligent wireless communications have obtained widespread attention, among which deep reinforcement learning (DRL) and deep learning (DL) are excellent machine learning technologies. They have great potential in enhancing the intelligence of wireless communication systems while overcoming the above challenge.
Both deep learning and reinforcement learning are closely related to the computational power of artificial intelligence. They are autonomous machine learning functions that pave the way for computers to create their own principles when coming up with solutions. These two types of learning may also coexist in several projects. Typically, deep learning uses current data, while reinforcement learning uses trial and error to compute predictions. The main difference between deep learning and reinforcement learning is their learning techniques. Taking the training set and further applying that learning to a new dataset is called deep learning. Reinforcement learning, on the other hand, can be implemented through continuous feedback-based action adjustments to maximize rewards.
Fig. 1.1 (Example 1) Design of a Deep-Unfolding Neural-Network for Intelligent Joint Optimization of RIS Beamforming

Fig. 1.2 (Example 2) Design of a DRL Neural-Network for Intelligent Joint Optimization of RIS Decision and Beamforming

Future wireless communication networks tend to be intelligentzed to accomplish the missions that cannot be preprogrammed. In the new intelligent communication systems, optimizing the network performance has become a challenge due to the ever-increasing complexity of the network environment.
Fig. 2.1 an Example of DRL-aided Communication System
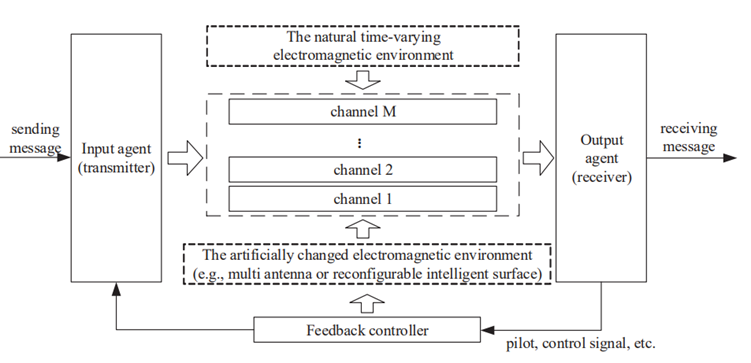
The endogenous security principle based on Dynamic Heterogeneous Redundancy provides a direction for the development of wireless communication security and safety technology. Endogenous safety and security (ESS or endogenous security) theory is to use the endogenous security structure with dynamic, heterogeneous, and redundant (DHR) attributes to realize the endogenous security function. Endogenous security theory not only can be used to resist known security threats, more importantly, but also can resist the unknown security threat and the unknown attack.
Fig. 3.1 Structures of DHR
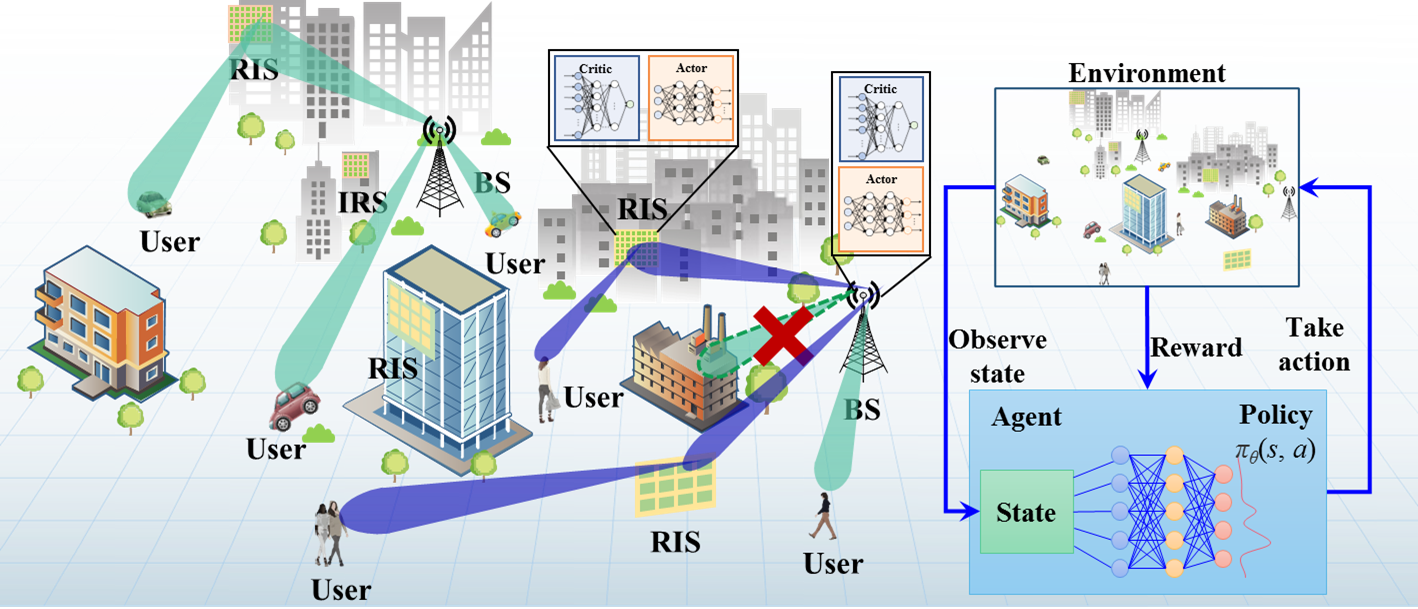
- Reconfigurable Intelligent surface (RIS)
RIS is one of our key research topics. RIS of meta material has the characteristics enabling to control electromagnetic waves effectively, fast and flexibly, which can enrich and amplify the DHR characteristics of electromagnetic environment to improve information security and functional safety. - Physical Layer Security (PLS)
The essence of the physical layer security transmission technology is to design a signal transmission and processing mechanism that is strongly as sociated with the wireless channel, so that only users on the legal channel can correctly demodulate the signal, while the signals on the channels in other locations are scrambled and unrecoverable.
Fig. 3.2 Components of RIS Fig. 3.3 PLS


Fluid antenna may represent any antennas equipped with software-controllable fluidic structure, and which can alter their shape and position to reconfigure the polarization, operating frequency, radiation pattern and other antenna performance metrics, and it may include designs involving no fluidic materials if they can mimic the agility. The figure illustrates the concept of a possible realization on a handset where conductive fluid is installed on a tube-like structure within which the fluid is free to move. In this design example, the shape of the antenna cannot be changed but its position can, which may be exploited for diversity and capacity benefits.
Please visit https://www.ee.ucl.ac.uk/fluid-antenna-systems/HOME.html for more information about fluid antenna.
Fig. 4.1 Fluid antenna in mobile device
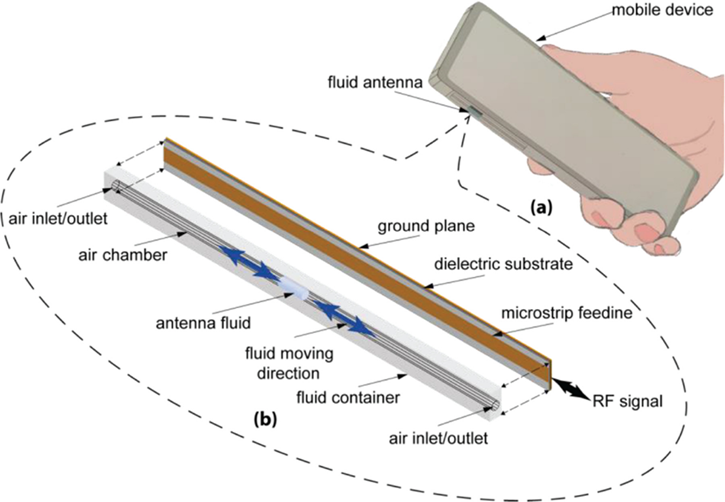
Fluid antenna takes advantage of spatial diversity as in MIMO but the received signal is taken from the best out of an extremely large number of antenna positions within a given space. Compared to MIMO, fluid antenna achieves the interference immunity through an extreme resolution of fading envelope and avoids the need for advanced signal processing that is normally required in MIMO antenna systems.
Fig. 4.2 Fluid antenna in communication system







