
Xixiang Lv, Professor, Ph.D.
Department:
School of Cyber Engineering
Address:
Post Box 106, Xidian University
No.2 Taibai Road South
Xian, Shanxi, China
710001
Email: xxlv@mail.xidian.edu.cn
Xixiang Lv, received her B.Eng in 2001, and Ph.D. in 2007, both from Xidian University. She has been a professor at Xidian University since 2015. She has published 18 high-quality papers, including prestigious IEEE journals and conferences. Her interests include information security, space information network security, and recently facial authentication, blockchain.
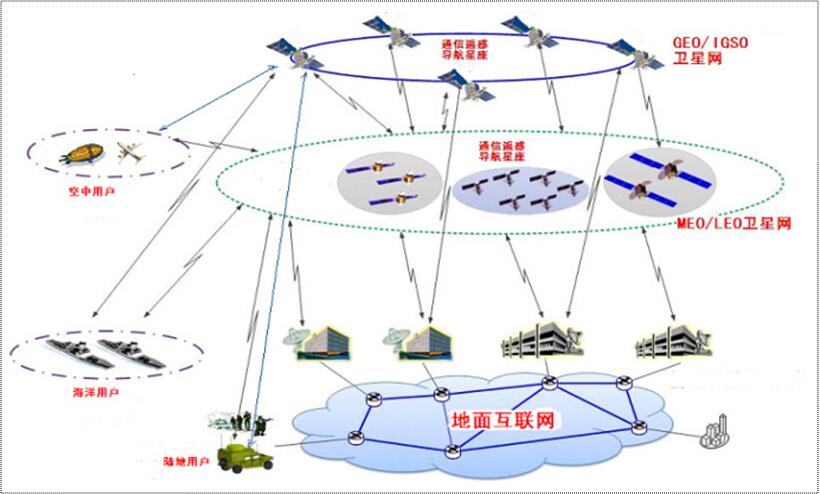
1. Security in Space Information Network
Space information network consists of many satellites at different orbits, ground stations, and clients. The security problems in space information networks mainly come from four perspectives, namely secure handoff, secure transmission control, key management, and secure routing, which involve many special designs due to characteristics of space information network, like latency and high error bit rate. Solving these problems would enable space information networks to enhance detection and transmission capabilities compared to the current single Earth observation satellite.
2. Security Issues in Facial Authentication Systems
Facial authentication systems are user-friendly and fast, which make them more appealing than passwords. However, they suffer from some inherent vulnerabilities that may compromise their security. These vulnerabilities mainly come from attacks at points of facial systems. For instance, spoofing occurs at sensor where artifacts may be present to the camera. Working toward these issues would lead facial systems to more promising applications

1. Xixiang Lv, Yi Mu, Hui Li, Loss-Tolerant Bundle Fragment Authentication for Space-based DTNs, IEEE Transactions on Dependable and Secure Computing, Accepted (8 Dec. 2014).
2. Xixiang Lv, Yi Mu, Hui Li, Non-interactive Key Establishment for Bundle Security Protocol of Space DTNs, IEEE Transactions on Information Forensics and Security, DOI 10.1109/TIFS.2013.2289993, Volume 9 Issue 1, 2014.
3. Xixiang Lv, Yi Mu, Hui Li, Loss-Tolerant Authentication with Digital Signatures, Security and Communication Networks, 9 (11): 366-383, 2014.
4. Xixiang Lv, Yi Mu, Hui Li, Key Distribution for Heterogeneous Public-key Cryptosystems, Journal of Communications and Networks, VOL. 15, NO. 5, October 2013.
5. Xixiang Lv, Hui Li, Baocang Wang, Authenticated Asymmetric Group Key Agreement based on Certificateless Cryptosystem, International Journal of Computer Mathematics, 91 (3):447-460, 2014.
6. Xixiang Lv, Hui Li, Secure Group Communication with both Confidentiality and Non-repudiation for Mobile Ad-hoc Networks, IET Information Security, 7(2), 2013.
7. Xixiang Lv, Hui Li, Baocang Wang: Virtual private key generator based escrow-free certificateless public key cryptosystem for mobile ad hoc networks. Security and Communication Networks, 6(1): 49-57 (2013).
8. Xixiang Lv, Hui Li: Group Key Agreement From Signcryption. TIIS 6(12): 3338-3351 (2012).
9. Xixiang Lv, Hui Li, Baocang Wang: Group key agreement for secure group communication in dynamic peer systems. J. Parallel Distrib. Comput. 72(10): 1195-1200 (2012).
10. Xixiang Lv, Hui Li, Baocang Wang: Identity-based key distribution for mobile Ad Hoc networks. Frontiers of Computer Science in China 5(4): 442-447 (2011).
11. Xixiang Lv, Hui Li: ID-based authenticated group key agreement from bilinear maps. Frontiers of Computer Science in China 4(2): 302-307 (2010).
12. Lv Xixiang, YANG Bo,“Traitor Tracing Using Identity Based Public-key Cryptography”。Chinese Journal of Electronics, Vol.15 No.4, 2006.(SCI:000241827000025,EI:064610241536)
13. Lv Xixiang, YANG Bo, “Broadcast Encryption Using Identity-based Cryptosystem”。Chinese Journal of Electronics,Vol.16 No.4, 2007. (SCI,EI)
14. Lv Xixiang, YANG Bo, "Broadcast Encryption Using Identity-based Public-key Cryptosystem". 2005 International Conference on Computational Intelligence and Security (CIS\'05). (SCI:000234874900163, EI:06229909484).
15. Lv Xixiang, YANG Bo, "Efficient Traitor Tracing Scheme Based On NTRU", the Sixth International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT\'05).(EI:06259953803,Outstanding Paper Award)






